Successful
Mobile App Deployment
The mobile development lifecycle doesn't stop once you create a mobile application and the mobile app development is complete. Mobile app deployment is a crucial phase during which critical tasks must be completed before a mobile app can be made available to end users. Getting mobile applications to end users is a critical part of any successful mobile deployment.
Daily
App Downloads

What is Mobile App Deployment?
The activities performed on a mobile application after mobile app development is complete is the mobile app deployment process. The process is complicated and involves many steps starting with the completion of mobile app development followed by rigorous testing that often involves manual testing and publication in a mobile application store such as Google Play or the Apple App Store. In fact, the deployment of mobile applications, as part of any mobile deployment effort, is often a massive undertaking, taking place on a global scale.
The mobile development lifecycle doesn't stop when mobile app development is complete. The process for deployment of mobile applications is a crucial phase during which critical tasks are completed before the mobile application is made available to end-users via app distribution.
Challenges of Mobile App Deployment
Deploying mobile applications is not as straightforward as deploying non-mobile applications, which are installed on web servers or any other compute devices that are fully controllable. Scanning for vulnerabilities, adding security controls, performing user acceptance testing, code signing, and adapting the mobile application for its unique app distribution channels are examples of activities that could be required to deploy a mobile application. The exact sequence of deployment activities that must be performed for a successful mobile app deployment depends on the use case. As a result of the non-uniform sequence of mobile deployment activities, the process to deploy a mobile application can be convoluted. Additionally, there is no one-size-fits-all process to deploy mobile applications. As a result, most organizations find this part of a mobile deployment incredibly challenging.
One of the challenges with mobile application deployments is that the responsibility for the various deployment activities is spread across disparate teams and there are multiple deployment options. Any successful mobile deployment requires much more than just rolling out mobile devices to end users after mobile app development is complete.
Deploying mobile applications is a critical component. Workflows to deploy mobile applications can be done by manually coordinating the required activities, but this is not scalable when you are deploying many mobile applications to multiple app stores, perhaps across geographies.
Secure App Delivery
For Mobile
App
Activities
Learn More About Deployment Activities
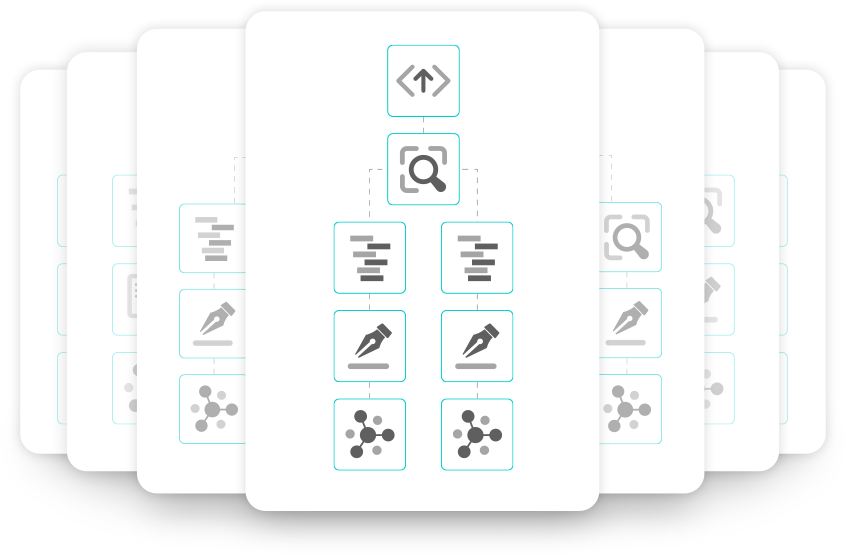
The common types of activities that may be performed to deploy the application after mobile app development is complete can be broadly classified into the following categories.
Import. This is when the mobile application is pulled into a deployment workflow after mobile app development is complete. It could happen manually (that is, the app is uploaded through a console) or automatically via integrations with build systems (CI/CD) or other app repositories.
Mobile App Enhancement. A requirement in many mobile app deployments is the addition of new functionality and configuration options to mobile apps. App-level mobile security is a common requirement for companies in the Financial Services, Healthcare, and Insurance verticals as mobile applications that use sensitive corporate data can be used on iOS and Android devices that may not have mobile device management (MDM). Without these device-level mobile management controls, companies cannot set device policies. No-code integration activities provide a convenient way to add functionality to a mobile application without having to send the app back to the developer to write new code. This convenience of adding new functionality after mobile app development is complete becomes especially valuable when deploying a mobile application sourced from third party independent software vendors (ISV). It is extremely unlikely that the ISV will create a mobile application version for each of their customers, as that creates an unwanted ongoing support burden for the ISV. Obtaining the mobile application’s source code can be prohibitively expensive for companies and requires a developer who must then become familiar with the mobile application’s code in order to add in security functionality.
Mobile Application Hardening. A mobile application can represent a significant intellectual property (IP) investment that a company will want to protect. Reverse engineering of an app is a way for others to steal this investment. App protection techniques, such as code obfuscation and anti-tampering, provide companies with a way to protect the IP investment in their mobile apps on any mobile device. Mobile application hardening is especially important for mobile applications deployed to mobile devices without mobile device management. That’s because companies cannot set device policies to secure these devices as they don’t have mobile management capabilities. Mobile application hardening is typically applied after mobile app development is complete.
Code Signing. Digitally signing mobile applications is a requirement for apps that go to app store(s). (e.g., the Apple App Store and Google Play Store.) and for installation on a mobile device. Anytime an app is modified it must be re-signed.
Testing. Collect user feedback, and automated functional testing and accessibility testing results from mobile applications testing services for mobile apps.
App Distribution. Pushing apps to app catalogs, public app stores (e.g., Google Play), or other app distribution mechanisms makes them available to end users. In the case of global distribution requirements, this may mean pushing different versions to different application containers in app stores and mobile deployments must be able to accommodate these differences.
As you see, the mobile application deployment options for iOS devices and Android devices can be quite involved.
Custom
Workflows
Deployment
Every Workflow is Unique
-

Dealing with UEM Controls
An unmodified mobile application needs to be signed and distributed to the application container in an enterprise app catalog to end users whose mobile devices are under UEM (Unified Endpoint Management) controls.
-

Accessing Corporate Data
Mobile applications that access corporate data and are used on unmanaged devices need app-level security controls. However, integrating controls into those mobile applications is very difficult without source code access, often an obstacle when dealing with third-party apps.
-

Protecting Investments and Proprietary Knowledge
A custom mobile application into which proprietary artificial intelligence (AI) models have been integrated is distributed to employees, partners and consultants across geographies through public app stores. Significant investments were made in creating the AI models, and it behooves the organization to prevent reverse engineering of the mobile app.
-

Gathering Feedback and Iterating Faster
Mobile applications ideally go through user acceptance testing before production rollout. When a mobile app is rolled out to employees through an enterprise app catalog there is often not a process to enforce the collection of user feedback or app review(s), so this crucial step is often skipped. As a result, apps in production will not reflect the improvements that could have been made from a pilot rollout that captures user feedback and app reviews programmatically.
Simplify
The Complex

Streamlined
Mobile App Deployment

Track all deployment activities to align teams and facilitate compliance reporting

Use existing workflows or build workflows that fits your organization

Add new functionality and use technologies integrations to extend the reach of workflows

Create a single source of truth by capturing all mobile a deployment data and providing visualizations

Analyze data and provide optimization insights to meet business objectives
Transform
Mobile App Deployments

Gain Visibility & Control
Visibility
Mobile application deployment platforms capture all mobile deployment data, starting with every step in a workflow down to the app version generated by workflow runs, and provides real-time visibility through the global dashboard and retroactive visibility through a digital audit trail. This serves as evidence for compliance and provides the ability to revert to the last good version of a successful deployment should the need arise.

Control
Platforms guarantee that mobile applications deployed have the controls and configuration options that organizations need without relying on developers or writing code, regardless of the source of the mobile app. These controls are added in after mobile app development is complete. Platforms ensure that a consistent set of activities are applied to mobile apps going through a deployment flow. Using a platform to orchestrate mobile deployment activities enforces rigor over app deployments, reduces the risk of missing critical tasks and increases successful mobile deployment costs by eliminating wasted efforts.
See Blue Cedar
In Action

Copyright © Blue Cedar. All Rights Reserved. | US and Non-European Privacy Policy | GDPR Privacy Policy | Various trademarks held by their respective owners.
